
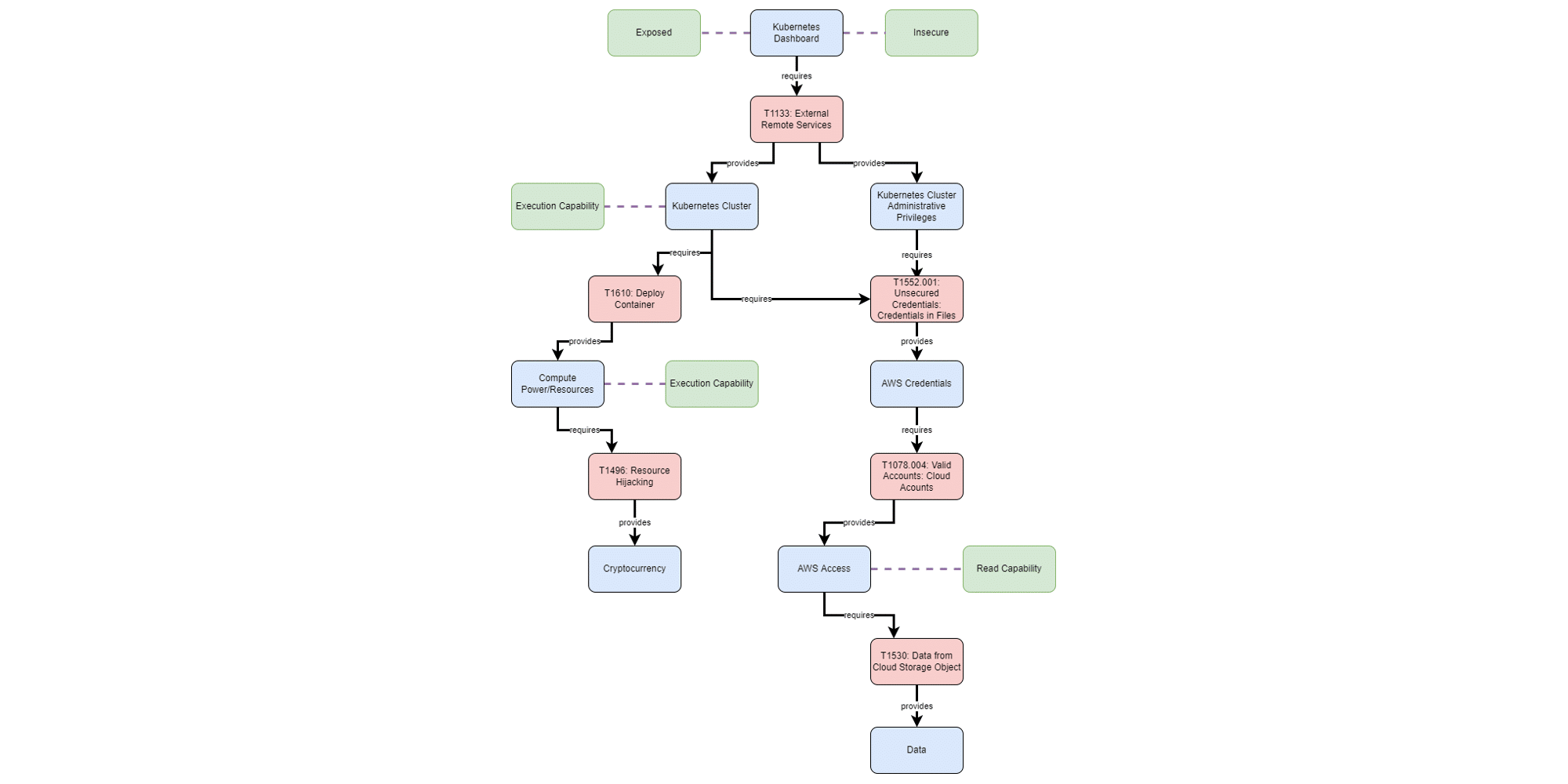
Research: Enterprise SIEMs Unprepared for 84% of MITRE ATT&CK Tactics and Techniques
25% of SIEM rules are broken and will never fire, due to fields that are not extracted correctly or log sources that are not sending the required data.

25% of SIEM rules are broken and will never fire, due to fields that are not extracted correctly or log sources that are not sending the required data.

In a recent SC Media column, Michael Mumcuoglu – CEO of CardinalOps, wrote how continuous improvement techniques can help CISOs more effectively manage the growing threat landscape and improve the visibility and effectiveness of their
I recently listened to an excellent summary about why MITRE ATT&CK has taken over the SOC world (sorry, it’s behind a paywall called “CSO Perspectives,” but this blog post is intended to summarize the key
At Black Hat 2022, our VP of Cyber Defense Strategy was interviewed on Security Guy TV to discuss why MITRE ATT&CK has become a standard way of describing your defensive posture to management as well
Summary This blog post summarizes new password stealing and impersonation risks recently discovered for Okta, along with recommended SIEM detection rules and associated MITRE ATT&CK techniques for SIEM solutions including Splunk, Microsoft Sentinel, IBM QRadar,
Summary This blog post summarizes Follina, an RCE zero-day discovered in Microsoft Office. It provides recommended detections in the native query languages for Splunk, Microsoft Sentinel, IBM QRadar, and Sumo Logic, along with associated MITRE

“Organizations need to become more intentional about detection in their SOCs. What should we detect? Do we have use cases for those scenarios? Do they actually work? Do they help my SOC analysts effectively triage

Dr. Anton Chuvakin Discusses “20 Years of SIEM – What’s Next?” Learn what Dr. Anton Chuvakin, Head of Security Solution Strategy at Google Cloud and former Gartner Research VP, has to say about questions like:
Spring into action (with SIEM detection rules for Spring4shell) The Spring Framework is an open source application framework that provides infrastructure support for developing Java applications. The framework can be used by any Java application

Image credit: World of Dictionary A new player has entered the game The ”Lapsus$” group, unknown before December 2021, has made multiple headlines in recent weeks, following multiple data breaches in big companies such as

Welcome to cyber-physical conflict The current situation in Ukraine demonstrates once again how the lines have blurred between cyber and physical conflict.

Anton Chuvakin, SIEM expert and former Gartner analyst (now at Google Chronicle) has written a thought-provoking blog post titled “SOC Threat Coverage Analysis — Why/How?“.