Security Layers lets you better prioritize detections based on coverage across your entire attack surface
What if you could:
- Measure the depth of your coverage based on the number of security layers – endpoint, network, email, IAM, cloud, containers, etc. – covered by your rules for a given sub-technique?
- Filter your ATT&CK coverage map based on specific security layers, so you could immediately identify the most critical gaps?
- Identify gaps due to missing telemetry from all relevant layers for a sub-technique?
Traditional MITRE ATT&CK coverage metrics and heat maps are too simplistic because they blindly add up the total number of detections aligned to a given technique — without measuring how much of the attack surface is actually covered by all your detections.
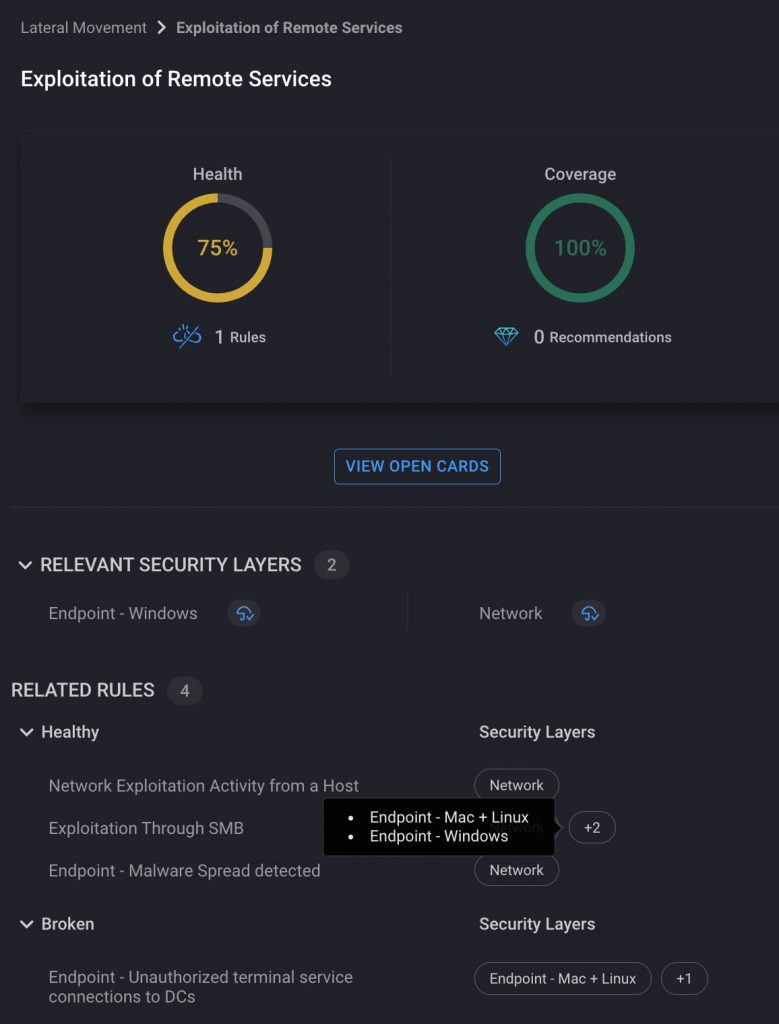
CardinalOps developed Security Layers to assess coverage with greater context around which aspects of your attack surface are most relevant to business priorities at a given point in time. It accomplishes this by mapping each detection to a specific security layer, and then enumerating the number of relevant layers covered for a given technique.
This enables SecOps teams to ensure they have “detection-in-depth” at multiple layers for the techniques that matter most to them. Additionally, Security Layers enable organizations to link their coverage to desired business outcomes by immediately identifying blind spots related to their most sensitive applications and data. It also reveals missing telemetry and data sources that can be incorporated into their detection strategy to increase depth of coverage.
In the example below, the user has selected Endpoint-Windows and Network as the most relevant layers for their organization. The technique “T1210: Exploitation of Remote Services” can be addressed via both of these layers (among others). Since the SIEM contains at least one detection addressing each of these layers, the coverage score is 100%.