“Organizations need to become more intentional about detection in their SOCs. What should we detect? Do we have use cases for those scenarios? Do they actually work? Do they help my SOC analysts effectively triage and respond? Detection use cases are the core of security monitoring activities. Having structured and repeatable processes is essential for prioritization, aligning monitoring efforts to security strategy, and maximizing the value obtained from your security monitoring tools.” Dr. Anton Chuvakin, Head of Security Solution Strategy, Google Cloud
Today we released our 2022 report on “The State of SIEM Detection Risk — Quantifying the Gaps in MITRE ATT&CK Coverage for Production SIEMs” and the results may — or may not — be surprising.
 This our second annual report in which we analyze anonymized data from production SIEM instances to get visibility into SOC preparedness to detect the latest adversary techniques in MITRE ATT&CK. And that’s important because detecting malicious activity early in the intrusion lifecycle is a key factor in preventing material impact to the organization.
This our second annual report in which we analyze anonymized data from production SIEM instances to get visibility into SOC preparedness to detect the latest adversary techniques in MITRE ATT&CK. And that’s important because detecting malicious activity early in the intrusion lifecycle is a key factor in preventing material impact to the organization.
The analysis shows that actual detection coverage remains far below what most organizations expect — and that many organizations are unaware of the gap between their assumed theoretical security and the defenses they actually have in place.
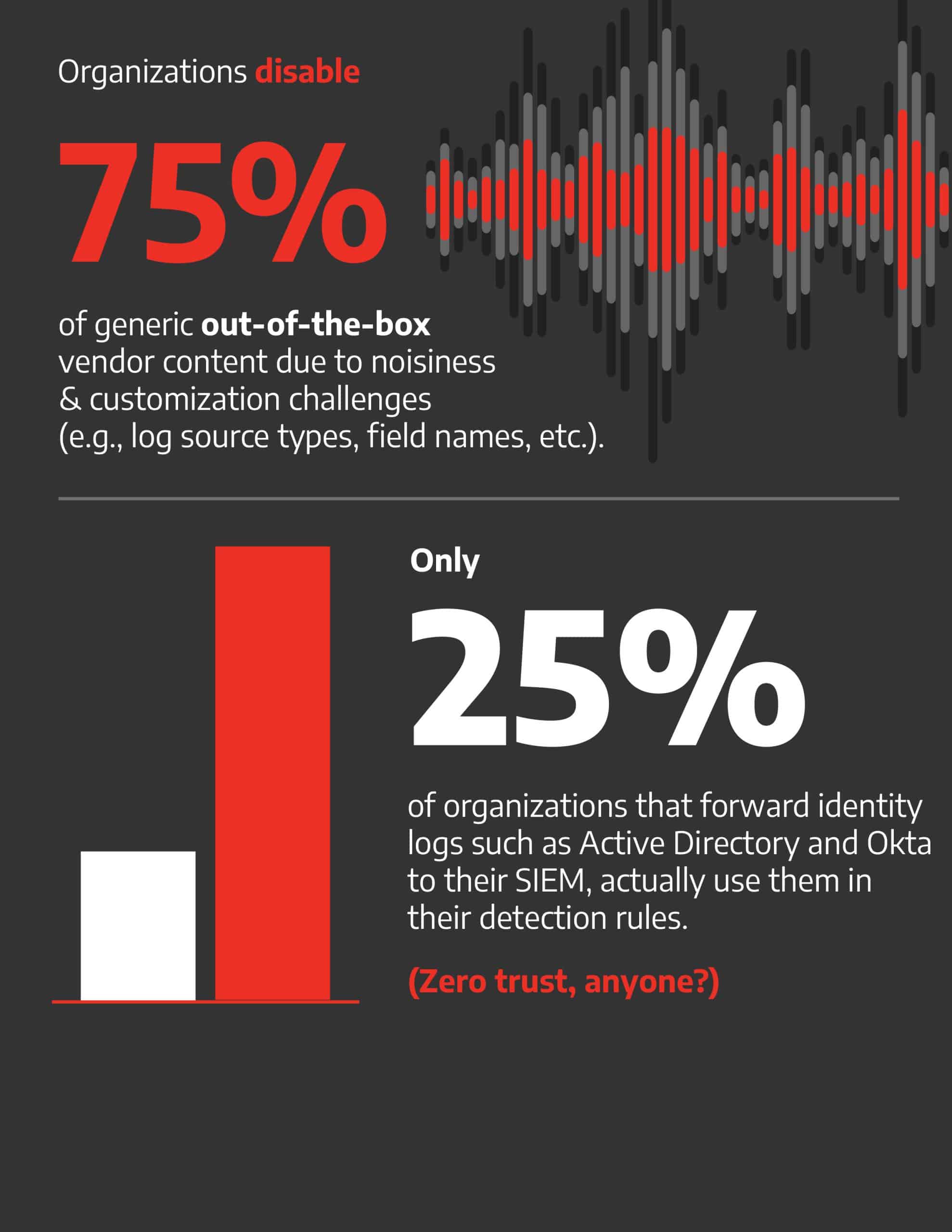
The data set for this analysis spanned diverse SIEM solutions – including Splunk, Microsoft Sentinel, and IBM QRadar – encompassing more than 14,000 log sources, thousands of detection rules, and hundreds of log source types, spanning diverse industry verticals including financial services, manufacturing, telecommunications, and MSSP/MDR service providers.
Our goal with creating this report was not to shame security teams for having blind spots, but rather to draw management-level attention to the disparity between perceived security and actual detection quality and coverage, using MITRE ATT&CK as the benchmark.
In particular, we believe we should be asking ourselves “If we’re spending all this time and money on more security tools, why are we still being hacked?”
Part of the answer lies in acknowledging that SIEMs are complex to configure, new log sources are constantly being added, and detection engineers find themselves struggling to keep up with the latest vulnerabilities and MITRE ATT&CK techniques.
In our minds, the answer lies in the need to apply automation and analytics to making our existing security stack more effective, rather than replacing the stack or adding new monitoring tools.
And applying automation and analytics to detection engineering and use case management is also aligned with what SOC teams have already done in other key areas such as threat intelligence and incident response.
So here are key results from our report — WDYT, are they surprising or not?

PS: Here’s what SC Magazine wrote today about the results of our report.