Centrally manage multiple SIEMs to ensure consistency & measure aggregate ATT&CK coverage
In an ideal world, most organizations would not choose to run two or more SIEM tools in the same environment. But, many do so for a range of reasons including:
- Cost-savings derived from a combination of cloud-native SIEMs (Microsoft Sentinel, Google Chronicle, etc.) and traditional SIEMs (Splunk, IBM QRadar, etc.).
- Multiple business units adopting their own SIEMs, either by choice or resulting from M&A activity.
- Regulatory requirements mandating local storage of sensitive data (e.g., EU data protection laws).

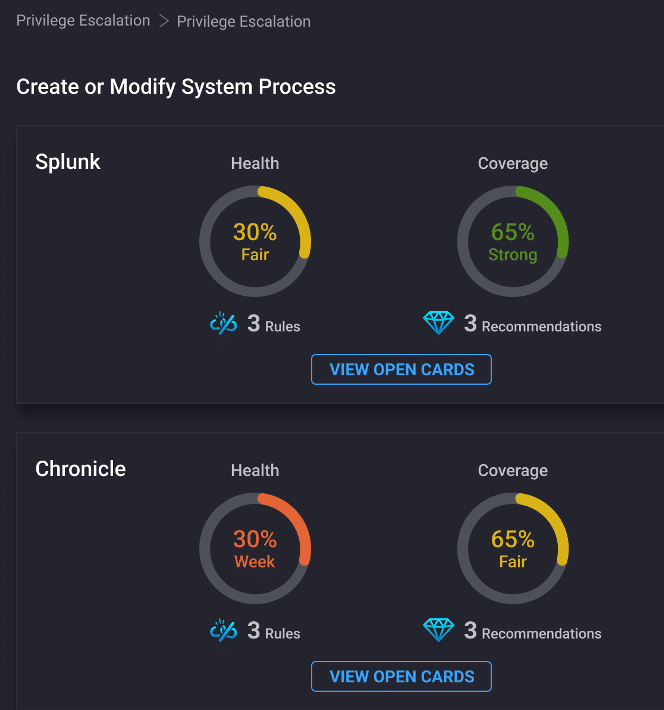
Security leaders want to understand their current detection posture so they can proactively identify high-priority gaps and remediate them in a prioritized manner. Gaining a federated or aggregated view across multiple SIEMs is essential for having an accurate understanding of your overall detection posture. But in a multi-SIEM environment consisting of Splunk + Microsoft Sentinel, for example, Microsoft security logs and alerts are sent to Sentinel (Defender for Endpoint, etc.) and all non-Microsoft telemetry (Proofpoint, Okta, CyberArk, Zscaler, Vectra, etc.) is sent to Splunk.
Each of these log sources requires its own detections, which cover different TTPs in the ATT&CK framework. So, if you’re only looking at one set of detections, you’re not getting a complete picture of your overall coverage and most critical gaps.
Additionally, security teams want to track the overall health of their detections across multiple SIEMs, since rules often break over time due to a range of reasons including misconfigured log sources, changes in log structures and field names, parsing errors, and filter changes (sensitive hosts, etc.).
CardinalOps can help you manage the complexity of multi-SIEM environments by:
- Providing a federated view of MITRE coverage and rule health across multiple SIEMs
- Ensuring consistent detections and log sources across multiple instances of the same SIEM.
- Automating SIEM migrations.
- Reducing ingestion costs by migrating log sources to the most appropriate SIEM.
- Identifying where to send alerts for organization-wide correlation, SOAR, and incident response.
