Leverage statistical analysis to reduce alert volume in the SOC
The only thing as bad as a rule that doesn’t fire when it should, is a rule that fires when it shouldn’t.
It’s like the boy who cried ‘wolf’ – noisy detections lead to alert fatigue which, according to a report conducted by International Data Corporation (IDC), results in complacency on the SOC team.
In fact, researchers found that 20-30% of all alerts are simply ignored or not investigated in a timely manner. It results in high burnout, high turnover, and low job retention of security professionals.
Noisy rules also give adversaries an easy path to exploit weaknesses in your defenses. According to SANS, an overwhelming majority of ethical hackers (more than 58%) can exploit and break into an environment in five hours or less – often by “hiding” their attacks in a cacophony of noisy detections that the SOC team regularly ignores.
Of course you can also deploy SOAR, alert triage, and other post-processing solutions to address this issue, but why not go after the source of noisy alerts – the “offending” rules themselves?
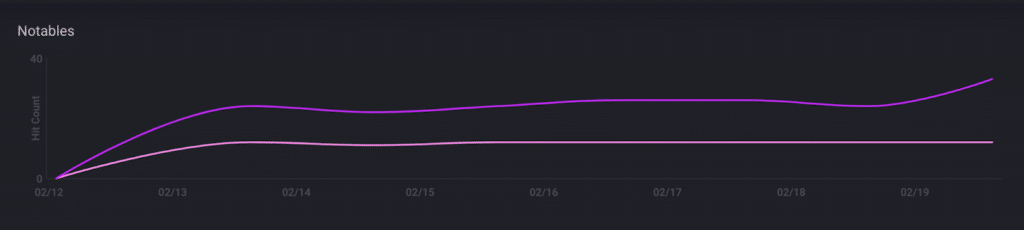
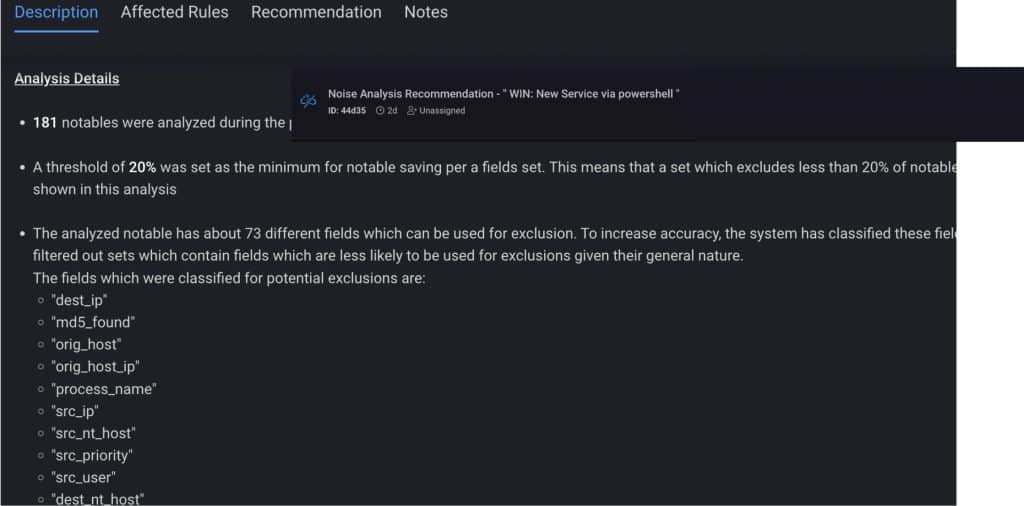
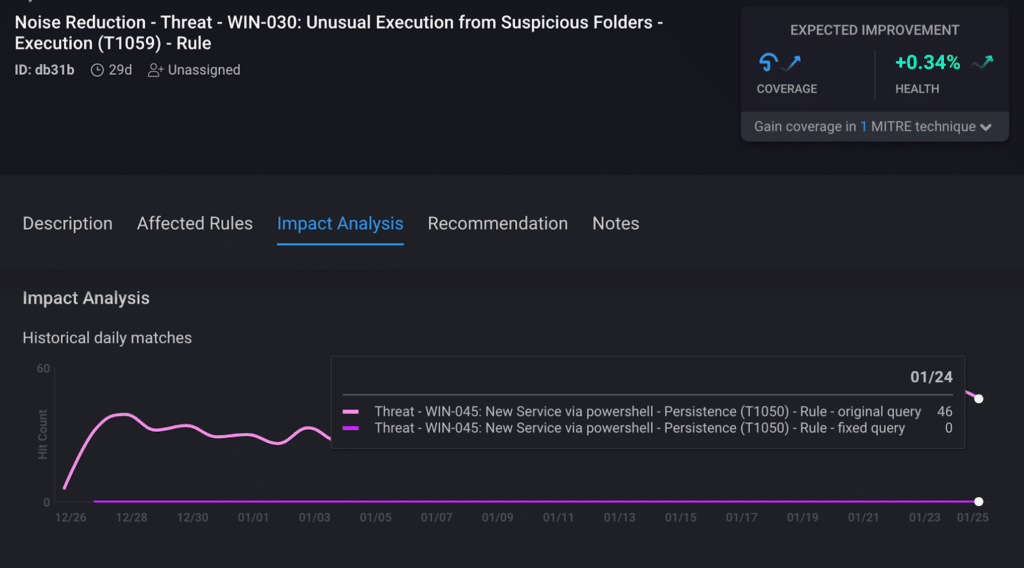
CardinalOps addresses the challenge of alert fatigue by analyzing all incidents created by the noisiest rules in your SIEM. To isolate the likely root cause of the problem, it looks for patterns and pinpoints specific field/value pairs that are responsible for triggering most of the alerts. It then provides recommendations on how to tune the rules using exclusions derived from the statistical analysis.
The end result? A meaningful reduction in alert volume – without eliminating alerts that are most likely to be true positives.