Welcome to cyber-physical conflict
The current situation in Ukraine demonstrates once again how the lines have blurred between cyber and physical conflict.
In fact, Ukraine has long been a proving ground for Russian cyber weapons. Notable examples include the wiper attacks on its critical infrastructure in 2015 and 2016; the wiper attack on banks in 2016; and the NotPetya wiper attack of 2017.
We’ve also learned recently that the Conti ransomware-as-a-service gang is aligned with the Russian government when they announced their support for the invasion of Ukraine — and pledged to retaliate against anyone targeting the Russian government in a cyberattack or “war activities.”
We’ve long suspected that Russian cybercriminal organizations operate with the Kremlin’s tacit approval – as long as they steer clear of Russian targets and are willing to aid government-backed hacking when called upon.
Preventing damage from friendly fire
So how do these groups prevent their attacks from indiscriminately striking Russian targets with “friendly fire”?
OSINT, IP address filtering, and ensuring that phishing attacks are only directed at western targets are only some of the ways this is accomplished.
In addition, malware typically checks for specific system conditions before executing. For example, the MITRE ATT&CK framework documents Virtualization/Sandbox Evasion (T1497) as a technique for avoiding detection by checking for security monitoring tools (e.g., Sysinternals, Wireshark, etc.) or other system artifacts associated with analysis or virtualization. Sub-techniques include System Checks (T1497.1), User Activity Based Checks (T1497.2), and Time-Based Evasion (T1497.3), in which the malware checks enumerates time-based properties such as uptime to check for virtualized environments.
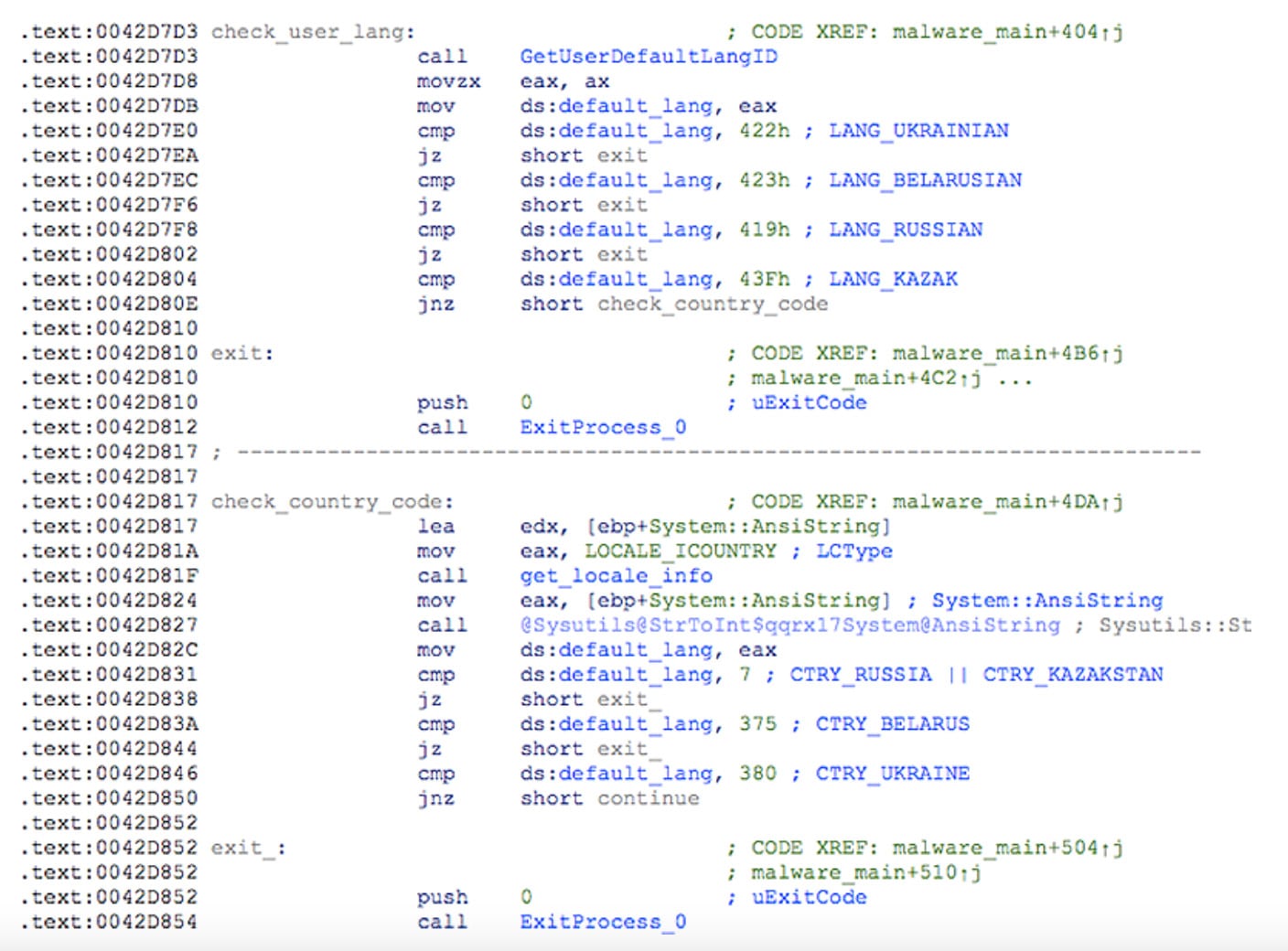
A similar mechanism is used to prevent Russian malware from compromising Russian hosts. In this case, the malware checks to see if the host OS has specific language packs installed, such as Russian, Belarussian, or Kazakh. And if they’re detected, the malware will exit and fail to install.
An example of this “anti-friendly fire mechanism” was revealed in the Kaseya ransomware attacks of 2021, which affected 1,500 organizations and was attributed to the REvil gang (the same gang linked to the attack that shut down JBS meat processing plants worldwide).
New HermeticWiper malware
A new type of malware called HermeticWiper was used against Ukrainian targets in the early hours of February 24, 2022 – the same day as the invasion by Russian troops. As we’ve seen in the past, it’s likely this malware will subsequently be used against western targets in the future – and we expect that it will also include checks for Russian-affiliated languages.
Summary and conclusions
Russian cyberattackers avoid “friendly fire” incidents in various ways including pre-execution checks for Russian language indicators on the host. These can include layout language, installed language packs, or other identifiers such as Russian DNS records or browsing history.
You can find the installation guide for the Russian language pack here. Note that the pack enables writing in Russian or choosing a Russian layout but does not affect existing settings.
Screenshot below: A CMP-JMP condition in malware designed to exit execution when detecting its presence on a Russian host.