A scalable, cloud-based platform for maximizing the efficiency and effectiveness of your existing SIEM/XDR
Using automation and MITRE ATT&CK, the CardinalOps platform continuously assesses your detection posture and eliminates coverage gaps in your SIEM/XDR – so you can easily implement a threat-informed defense.
What’s more, it drives cost savings by recommending new ways to tune noisy and inefficient queries, reduce logging volume, and eliminate underused tools in your stack.
Your SIEM/XDR
- Splunk
- Microsoft
- IMB
- Google
- Crowdstrike
- Sumo Logic
with SIEM/XDR
Detection Posture Management Platform
-
ATT&CK Rule Mapping Engine
-
Prioritization Engine for New Detections
-
Analysis Engine for Noisy or Broken Rules & Misconfigured Data Sources
-
Rule Simulation Engine
-
Reporting Engine
Curated Rule DataBase
5,000+ Best Practice Rules
Continuously expand your MITRE ATT&CK coverage based on your business priorities and risk
- ATT&CK Mapping Engine
No spreadsheets required - Prioritization Engine
Gain new high-fidelity detections - Analysis Engine
Identify broken and noisy rules - Rule Simulation Engine
Test rules before deployment - Reporting Engine
Validate your detection posture - Curated Database
Best practice detections
 ATT&CK Mapping Engine
ATT&CK Mapping Engine
No spreadsheets required
No spreadsheets required
The first step is mapping all your existing rules to ATT&CK – including custom rules – and calculating your detection coverage.
By evaluating the log sources in a given rule and using clustering techniques to compare rules to other rules in our proprietary database, CardinalOps’ mapping engine finds the “best fit” for a rule in the existing framework of ATT&CK techniques.
To evaluate the “depth” of coverage for a given technique or sub-technique, CardinalOps goes beyond simply adding up the number of rules.
Instead, it examines how many relevant security layers – endpoint, network, email, IAM, cloud, etc. – are covered by existing rules for each technique and sub-technique.
This enables you to evaluate your existing coverage compared to your potential coverage (data sources you’re currently using), as well identify additional telemetry sources that can be used to strengthen your coverage, based on your priorities.
 Prioritization Engine
Prioritization Engine
Gain new high-fidelity detections
Gain new high-fidelity detections
Based on the priorities you have specified – such as APT groups, specific tactics or techniques, security layers (endpoint, network, email, IAM, cloud, etc.), log source types (AWS, Okta, etc.) etc. – the platform delivers new detections to address critical coverage gaps.
Detections are delivered in a high-fidelity, deployment-ready format. This means they are delivered in your SIEM’s native query language – not a generic format like SIGMA – and have been pre-customized for your unique environment (data sources, naming conventions, fields, indexes, etc.).
Equally important, they have been pre-validated to not cause excessive noise in the SOC, based on your historical log data.
 Analysis Engine
Analysis Engine
Identify broken and noisy rules
Identify broken and noisy rules
All rules have specific prerequisites to enable them to fire. For example, the logs must be ingested by the SIEM/XDR, the required field values must appear in the logs, and the parsing must be correct.
The CardinalOps platform has a series of automated validators to check for these prerequisites. However, the platform doesn’t simply identify issues, it provides detailed recommendations on how to fix broken rules. And if the fix can be implemented in the rule itself, it provides the mitigated rule in a pre-validated state that you can instantly push to your SIEM, after you have reviewed it.
Noisy rules are a little different – because every environment is different and only your team has the full context to understand exactly what changes in the environment have led to the rule becoming noisy. To accelerate your workflow, the platform performs a statistical analysis on the noisiest rules to pinpoint specific field/value pairs that are most responsible for triggering the alerts. It then provides recommendations on how to tune the rules using exclusions derived from the statistical analysis.
 Rule Simulation Engine
Rule Simulation Engine
Test rules before deployment
Test rules before deployment
All new and mitigated rules are subjected to an automated Impact Analysis before deployment. This process simulates the alerts that would have been generated over the past 90 days (or other customizable period) – based on your historical log data – had the new or mitigated rule been in place in your SIEM/XDR. The purpose of this automated check is to ensure that the new or mitigated rules won’t generate unnecessary noise or false positives.
Additionally, each new rule recommendation documents a series of validation steps that can be taken in your environment to trigger the rule (such as adding a new MFA option to an existing user in your Active Directory admin console, which can be an indication of malicious activity).
Some organizations also go through an extra step before deploying new rules to their SIEM/XDR, whereby they deploy them in “silent mode” that only generates email alerts to the detection engineering team rather than creating notables (incidents or offenses) for SOC analysts. This configuration is directly managed in the CardinalOps console and is typically used for a week or so before the rule is fully deployed.
Deployment of new and mitigated rules can also be restricted to specific change windows that you specify based on your organizational procedures. Some organizations also leverage the CardinalOps platform API to push new rules into production via GitHub CI/CD workflows rather than from a button in the CardinalOps console.
 Reporting Engine
Reporting Engine
Validate your detection posture
Validate your detection posture
The platform includes a series of reports for validating your organization’s detection posture and answering common questions from leadership such as “How exposed are we?” and “How prepared are we to detect the latest threats?”
These reports are also essential for driving and tracking continuous improvement in ATT&CK coverage over time, based on your organizational priorities.
 Curated Database
Curated Database
Best practice detections
Best practice detections
The platform relies on a database of more than 5,000 best practice detections that have been curated over time by our team of world-class security researchers with nation-state expertise.
Platform users can also search our rule catalog using specific parameters of interest such as Technique number, CVE, log source type, application, etc.
Integrates quickly via SIEM/XDR APIs
Setup time is typically less than an hour because the platform easily integrates via the native API of your SIEM/XDR. This enables it to quickly query the SIEM/XDR to understand its detection ruleset, log sources, and other metadata.
There are no agents to deploy or appliances to configure. Sensitive log data never leaves the SIEM/XDR, and the platform is SOC-2 certified.
The detection posture for multiple SIEM/XDR instances can also be managed from a single console. This enables a federated view of ATT&CK coverage and rule health across multiple instances; automated consistency of rulesets and log sources across multiple instances; and automated SIEM/XDR migrations.
Our platform supports popular enterprise SIEM/XDR solutions including:
- enterprise
cloud
enterprise security (ES) - Sentinel
- IBM QRadar
IBM QRadar on Cloud (QRoC) - Chronicle SIEM
- Falcon LogScale
- Log Analytics
- + new integrations being added all the time
with SIEM/XDR
Built on MITRE ATT&CK
Everything we do is based on MITRE ATT&CK, which has become the standard framework for understanding adversary behaviors, communicating with other teams – and building a threat-informed defense.
We are not simply a consumer of MITRE ATT&CK, we are also a contributor to the ATT&CK defender community. Our security research team, composed of world-class security experts with nation-state expertise, has contributed multiple sub-techniques to the ATT&CK framework during its ongoing evolution.
Continuously evaluating your detection posture vis-a-vis ATT&CK is essential because – big “surprise” – adversary techniques are constantly evolving. Case in point: the ATT&CK framework began with just 97 techniques and v12 now encompasses more than 500 techniques and sub-techniques.
Your Command-and-Control Center
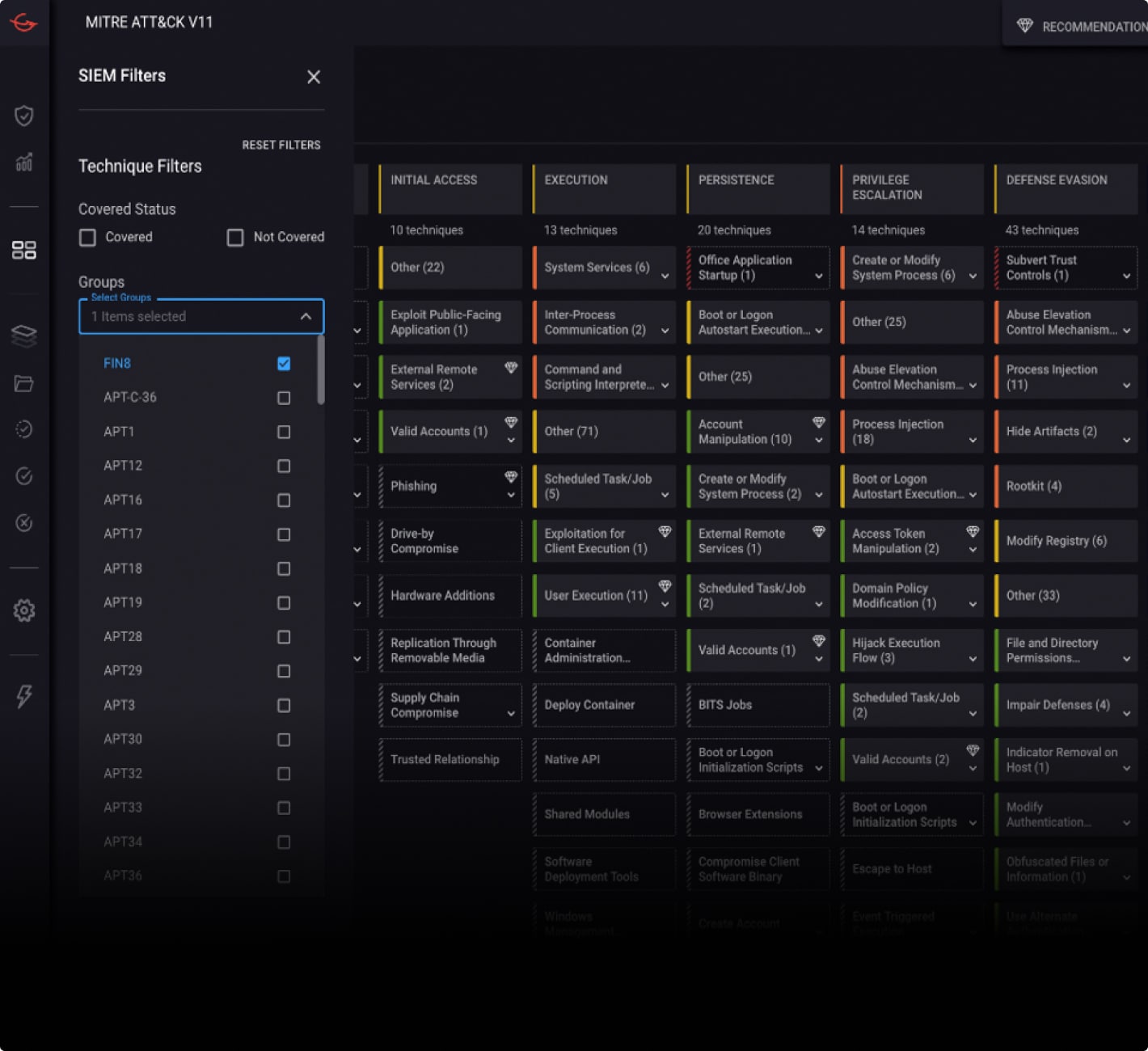
The CardinalOps console provides an overall view of your rule coverage and health, which can be filtered based on your organizational priorities to focus on specific areas of interest (such as APT groups targeting your sector).
You can also drill down into any technique on the ATT&CK map and view the platform’s recommendations for new detections (to address gaps), as well as mitigations for broken and noisy detections, and cost saving recommendations.
You can drill down into any recommendation to see the full rule in the native query language of your SIEM. Rules are automatically customized to your environment (log sources, indexes, naming conventions, etc.).
Each recommendation includes a description of the type of attack it detects, which tactics, techniques, and APT groups it covers, and a test workflow to see how often the rule would have fired in the past 90 days, based on historical log data.
Once you have reviewed and approved the rule, you can push it directly into your SIEM from the CardinalOps console.