Eliminate broken rules that will never fire – and remediate them instantly
If you’re like most detection engineering teams, you’re continuously adding new detection rules to your SIEM. But over time, your environment has changed in different ways.
Your network has changed, your security tools have been upgraded to newer versions and log formats, older log sources have been retired, and your monitoring targets have changed.
And you may even have added generic rules that were copied and pasted from open sources or by an MSSP (and might contain ReGex errors that prevent proper parsing).
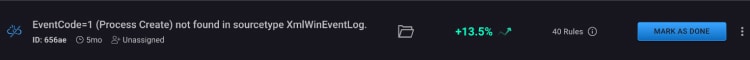
The result? Broken rules that will never fire due to misconfigured data sources, missing fields, parsing errors, and other data quality issues – creating additional gaps in your coverage.
This leads to a false sense of security because your CISO and SecOps team thinks they’re protected — but then are surprised when your Red Team (or worse, an adversary) finds a hidden gap in your defenses and exploits it.
The CardinalOps platform uses specialized analytics to continuously analyze all your rules to ensure they have all required prerequisites to fire (log data, field values, etc.). But it doesn’t just identify issues with broken rules, it delivers remediated rules that you can review, test and instantly deploy into your SIEM.
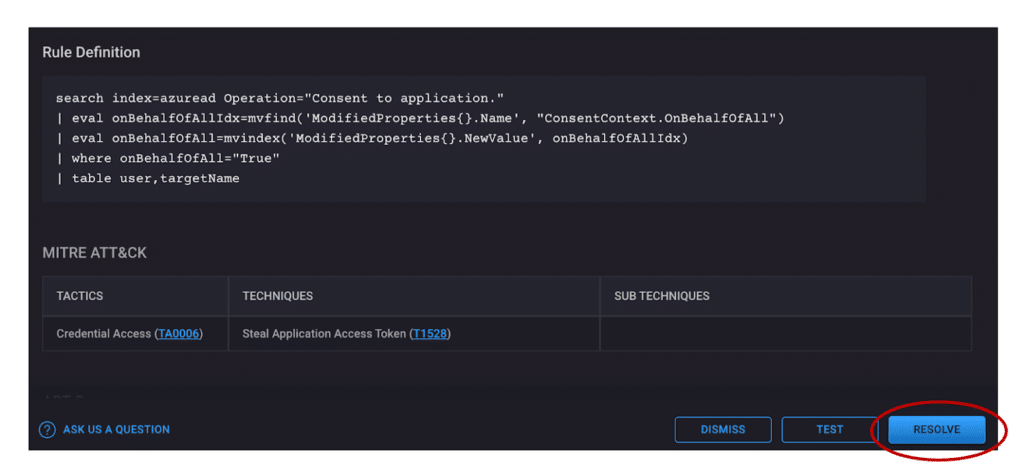
And if remediation requires actions outside your SIEM – such as enabling event logging options on endpoints that were previously turned off – it delivers detailed recommendations on how to fix it, with links to technical documentation you can share with your IT team.
