Summary
This blog post summarizes Follina, an RCE zero-day discovered in Microsoft Office. It provides recommended detections in the native query languages for Splunk, Microsoft Sentinel, IBM QRadar, and Sumo Logic, along with associated MITRE ATT&CK adversary techniques.
A tale as old as desktop computing
Most users interact with Office documents on a daily basis, making Office documents a popular attack vector among nation-state APTs and cybercriminals alike. For years, attackers have been weaponizing Microsoft Office documents in different and innovative ways, ranging from embedding OLE2 link objects to malicious macros or exploiting different zero-days.
A wild vulnerability appears!
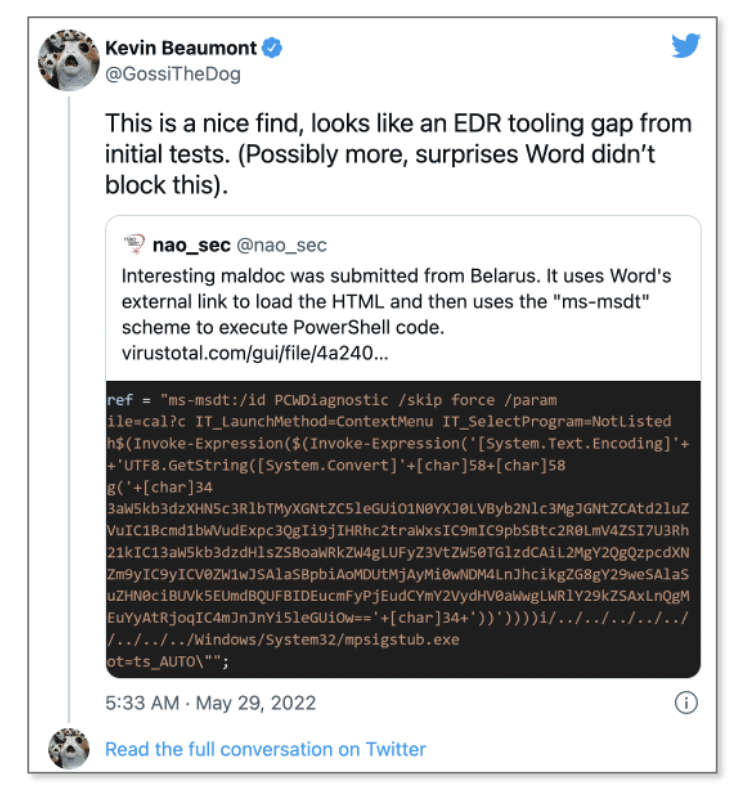
On May 29th, a researcher found an odd looking Word document in VirusTotal and decided to look into it. The document uses the Word remote template feature in order to retrieve an HTML file from a remote server. The HTML file uses the ms-msdt MSProtocol URI scheme to load code and execute a PowerShell script (MITRE ATT&CK T1059.001).
This RCE vulnerability was dubbed “Follina” and later received the CVE CVE-2022-30190. It can be exploited even when macros are disabled.
Microsoft’s Diagnostic Troubleshooting Wizard (MSDT) is a built-in tool in Windows operating systems. MSDT can be used either as a standalone program, as a standalone command, or as part of a script. More information about MSDT can be found here.
Here’s an example of a malicious Russia-themed document that was uploaded to VirusTotal in April:

Proofpoint has also reported that Chinese APT group TA413 is exploiting this vulnerability in the wild.
Mitigation
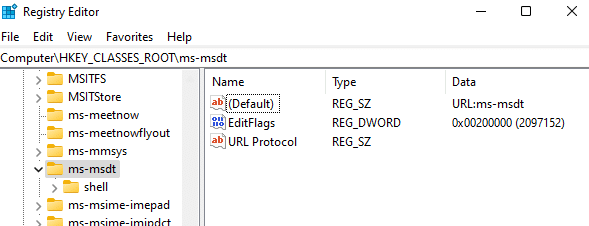
The workaround used to mitigate this vulnerability right now is to break the relationship between ms-msdt MSProtocol URI scheme and MSDT.exe.
This can be done by removing HKEY_CLASSES_ROOTms-msdt registry key via the regedit tool or the command line. Make sure to take note of the keys and values in order to be able to restore them after the vulnerability is patched or mitigated by Microsoft. For more information about this mitigation read Microsoft’s post on the matter.
Screenshot below: The registry key that can be deleted to mitigate the vulnerability.
SIEM Detections
Because the Office document does not contain the malicious payload, it might be difficult for anti-virus and EDR software to detect malicious documents attempting to exploit this vulnerability.
As explained in the technical analysis by Huntress, when exploiting this vulnerability, the Office application spawns MSDT.exe as a child process. This can be detected using the following queries in the respective SIEMs:
Splunk
index=[WindowsIndex] sourcetype=WinEventLog EventCode=4688 New_Process_Name=*msdt.exe Creator_Process_Name IN (*winword.exe, *excel.exe, *powerpnt.exe ) “msdt”
| stats values(Creator_Process_Name) as Creator_Process_Name, values(Account_Name) as Account_Name, values(dest_ip) as dest_ip count by ComputerName
Microsoft Sentinel
SecurityEvent
| where EventID == 4688
| where (ParentProcessName contains “winword.exe” or ParentProcessName contains “excel.exe” or ParentProcessName contains “powerpnt.exe”) and NewProcessName contains “msdt.exe”
| project TimeGenerated, SubjectAccount, Account, Computer, CommandLine, ParentProcessName, NewProcessName
IBM QRadar AQL
select QIDNAME(qid) as “Event Name”,logsourcename(logsourceid) as LogSource, “New Process Name”, “Creator Process”, sourceip, sourceport, destinationip, destinationport, username, DATEFORMAT(starTTime,’YYYY-MM-dd HH:mm:ss’) as startTime from events
where devicetype=12 and “EventID”=4688 and “Creator Process” in (‘winword.exe’, ‘excel.exe’, ‘powerpnt.exe’) and “New Process Name” = ‘msdt.exe’
Note: the field “Creator Process” and “New Process Name” might be named differently in every QRadar instance.
Sumo Logic
_sourceCategory=*windows* AND “msdt”
| json field=_raw “EventID” as EventID nodrop
| json field=_raw “Computer” as Computer nodrop
| json field=_raw “EventData.NewProcessName” as NewProcessName nodrop
| json field=_raw “EventData.ParentProcessName” as ParentProcessName nodrop
| toLowerCase(NewProcessName) as NewProcessName
| toLowerCase(ParentProcessName) as ParentProcessName
| where EventID = “4688” and (ParentProcessName contains “winword.exe” or ParentProcessName contains “excel.exe” or ParentProcessName contains “powerpnt.exe”) and NewProcessName contains “msdt.exe”
| count by Computer, ParentProcessName, NewProcessName
Conclusion
As with most of the Microsoft Office exploits over the years, Follina relies on the end user executing a malicious file (MITRE ATT&CK T1204.02) in order to exploit a vulnerability and run a malicious payload (MITRE ATT&CK T1204.02).
There will always be a ”arms race” between malicious actors and blue teams. New exploits will give rise to new detections and mitigations. The only way to break the chain is to continuously educate users about the risks of interacting with attachments or links from unknown users and websites.