Simplify Onboarding & Ongoing Management for Google SecOps SIEM (formerly Chronicle)
CardinalOps + Google SecOps SIEM (formerly Chronicle)
Backed by detection engineering experts with nation-state expertise, the CardinalOps platform integrates easily with your Google SecOps SIEM via the SIEM’s native API and Google BigQuery.
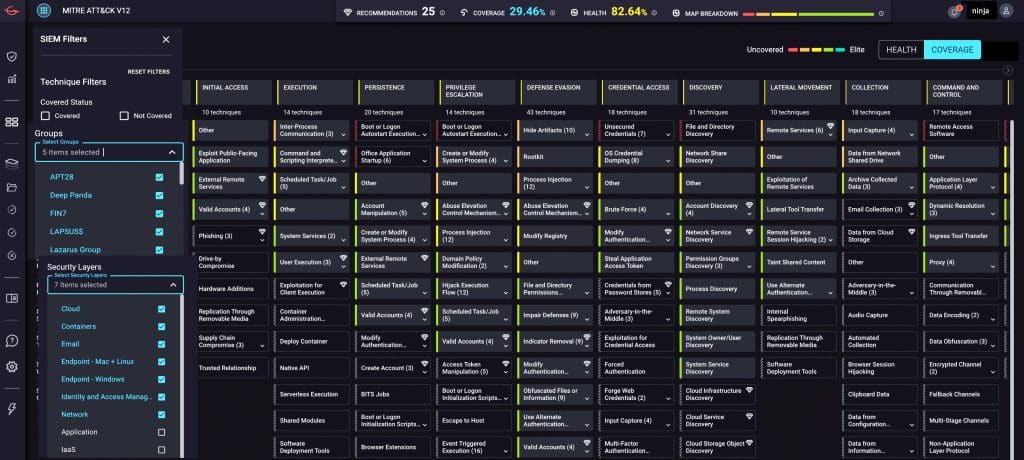
Leveraging specialized analytics, automation, and MITRE ATT&CK, our cloud-native platform continuously ensures you have the right detections in your Google SecOps SIEM and they’re always working effectively.
Rapid onboarding
- Understand what data sources you need to add curated detections from GCTI
- Gain insights into what data is missing to implement custom detections
- Migrate critical detections from other SIEMs (e.g., Splunk)
- Map both curated and custom detections to MITRE ATT&CK
Interested in accelerating your migration to Google SecOps SIEM?
Learn how the CardinalOps platform continuously assesses your Google SecOps SIEM (or other SIEMs – Splunk, Microsoft Sentinel, IBM QRadar, etc.) — using MITRE ATT&CK as the benchmark — to identify security control configuration gaps from missing, broken, and noisy rules that leave your organization exposed.
Schedule a demo with one of our cybersecurity experts to see how the CardinalOps platform can streamline your Google SecOps SIEM onboarding.
Continuously validate & improve detection coverage
- Identify & remediate issues that lead to ineffective rules and blind spots
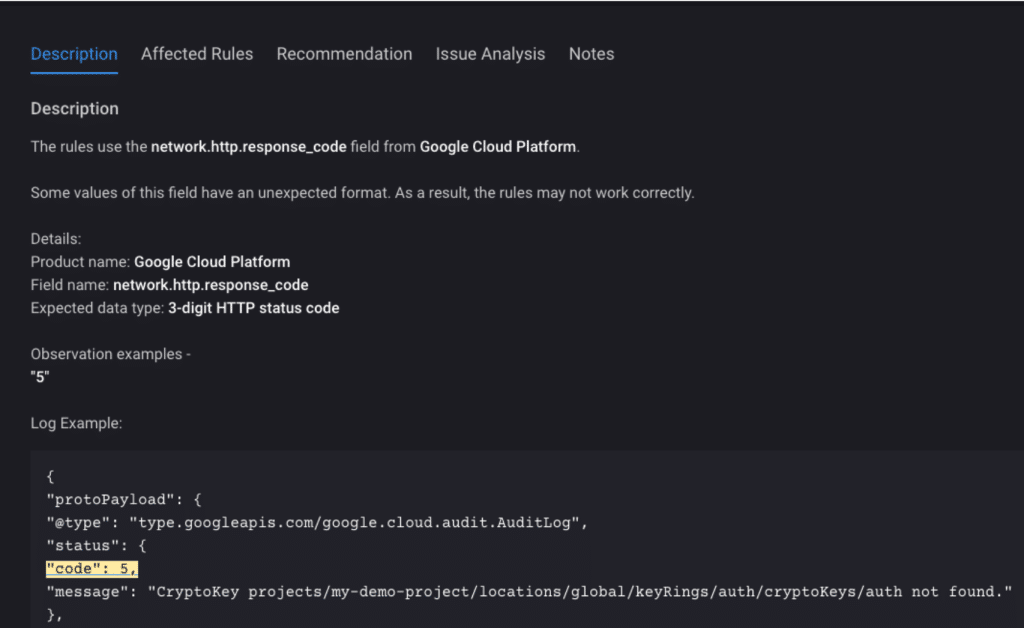
- Telemetry health (missing fields, stale log sources, etc.)
- Rule health (scheduling, reference sets, parsing, asset coverage, etc.)
- Tune noisy rules
- Pinpoint key coverage gaps based on your priorities (APTs, crown jewels, etc.)
- Add new rules in native YARA-L from CardinalOps’ best practice repository
- Benchmark your SIEM using the ATT&CK framework as it evolves over time
3rd Annual Report on the State of SIEM Detection Risk: Benchmark your SIEM’s MITRE ATT&CK detection coverage and rule health based on our analysis of real-world data from production SIEMs covering more than 4,000 detection rules, nearly one million log sources, and hundreds of unique log source types.