If you’re like most of us in the defender community, you’re probably tired of seeing all the colored heat maps used to represent MITRE ATT&CK detection coverage.
And while there’s some debate about whether heat maps should even be used with management teams, there’s clear agreement we need to accurately track our coverage and proactively close gaps based on a threat-informed defense and what’s most important to our organizations.
This strategy to developing new detections based on business priorities and risk is considered superior compared to more reactive or ad hoc approaches (typically driven by whoever yells the loudest in the organization).
Part of the skepticism around traditional ATT&CK heat maps (such as those from Splunk and other SIEM vendors) is that darker colors in all the boxes doesn’t necessarily equate to better security.
We need a better way to assess coverage with greater context around which aspects of our attack surface are most important at a given point in time — as well as which APT groups are most relevant — because most organizations recognize it’s an iterative process during which we continuously increase coverage over time.
That’s why we developed a new approach for measuring detection posture and identifying critical gaps using MITRE ATT&CK Security Layers. In our definition, security layers are defined to be various dimensions of your attack surface such as endpoint, network, email, IAM, cloud, and containers.
Why MITRE ATT&CK Matters
As the standard framework for understanding adversary playbooks and behavior, MITRE ATT&CK now describes more than 500 techniques and sub-techniques used by threat groups such as APT28, the Lazarus Group, FIN7, and LAPSUS$.
According to ESG research, 89% of organizations currently use MITRE ATT&CK to reduce risk for security operations use cases such as determining priorities for detection engineering, applying threat intelligence to alert triage, and gaining a better understanding of adversary tactics, techniques, and procedures (TTPs).
Why a New Coverage Metric is Required
Traditional MITRE ATT&CK coverage metrics and heat maps are too simplistic because they blindly add up the total number of detections aligned to a given technique — without measuring how much of the attack surface is actually covered by all your detections.
In the traditional approach, for example, having 5 endpoint detections aligned to a given technique counts the same as having 5 detections but with each one covering a different layer. This is important because we want to cover multiple layers in the attack surface rather than concentrating all our detection rules on just one or two layers like the endpoint and network layers, since this leads to gaps that attackers can exploit at other layers like cloud and IAM.
Getting to Detection-in-Depth
Developed by CardinalOps, MITRE ATT&CK Security Layers dramatically extends the concept of ATT&CK coverage by measuring the “depth” of detection coverage for the first time.
It does this by mapping each detection to a specific security layer — Windows, Linux, MacOS, network, email, IAM, cloud, containers, SaaS, IaaS, etc. — and then enumerating the number of relevant layers covered for a given technique.
This enables SecOps teams to ensure they have “detection-in-depth” at multiple layers for the techniques that matter most to them.
Additionally, Security Layers enable organizations to link their coverage to desired business outcomes by immediately identifying blind spots related to crown-jewel assets, such as their most sensitive applications and data.
It also reveals missing telemetry and data sources that can be incorporated into their detection strategy to increase depth of coverage.
Coverage tracking using Security Layers is built into the CardinalOps automation platform, which continuously audits the rule set of existing SIEM/XDRs and groups them into their respective layers for each ATT&CK technique. The platform integrates natively with major SIEMs including Splunk, Microsoft Sentinel, IBM QRadar, Google Chronicle SIEM, CrowdStrike Falcon LogScale, and Sumo Logic.
CardinalOps has contributed to the MITRE ATT&CK community in the past by providing new sub-techniques that were subsequently incorporated into the standard ATT&CK framework.
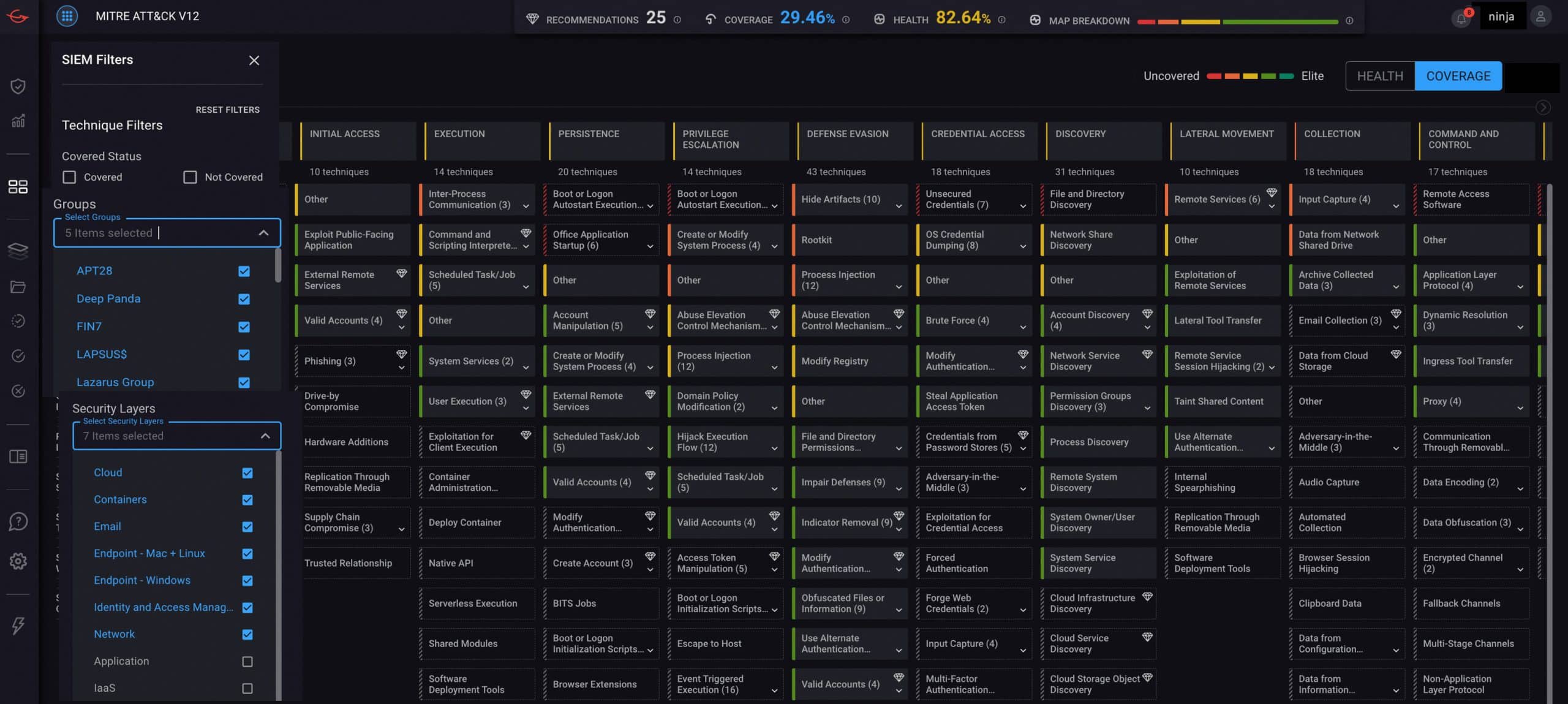
MITRE ATT&CK coverage map from the CardinalOps platform showing filtering by relevant APT Groups and Security Layers. Metrics at the top show current coverage as a percentage of all relevant techniques, based on selected filters, as well as overall health of detections. Health is measured as the number of working detections — e.g., all required log sources are being ingested, required fields are present in the logs, fields are being parsed correctly, etc. — as a percentage of total number of detections.
Adding Context and Detail to MITRE ATT&CK
Jon Oltsik is a veteran industry analyst who’s written extensively about MITRE ATT&CK in CSO and other industry publications. His comment on Security Layers:
“Security layers add context and detail to the MITRE ATT&CK framework and associated detection rules. In this way, CardinalOps can help organizations further focus their attention on detecting the tactics, techniques, and procedures (TTPs) of adversaries most likely to target their organizations. This can help reinforce security defenses in critical areas – especially for understaffed organizations lacking advanced cybersecurity skills and resources.”
How Automation Helps Operationalize MITRE ATT&CK
Until recently, many organizations have struggled with operationalizing MITRE ATT&CK in their day-to-day operations because they had to rely on manual approaches like spreadsheets and open source tools to measure their coverage and identify blind spots.
Using automation and specialized analytics, the CardinalOps platform helps organizations continuously measure and improve their detection posture using MITRE ATT&CK Security Layers. Coverage can be filtered based on organizational priorities such as Security Layers as well as by other key risk parameters such as APT groups or specific Tactics and Techniques.
The platform further helps eliminate coverage gaps by providing high-fidelity detections and recommendations to address missing, broken, and noisy detections.
Summary
SecOps teams are looking for a more precise and holistic approach to measure their MITRE ATT&CK detection posture and identify gaps based on organizational priorities and desired business outcomes.
We’re proud to be helping the ATT&CK community find new and innovative ways to ensure organizations always have the right detections in place to defend against our most important adversaries.
About CardinalOps
Most security vendors pitch you on replacing your stack or adding new monitoring tools to it. CardinalOps has a more practical approach.
Founded by security experts with nation-state expertise and led by executives from leaders such as Palo Alto Networks, Microsoft Security, and IBM Security, CardinalOps is focused on maximizing the effectiveness and efficiency of your existing security stack.
Using automation and MITRE ATT&CK, the CardinalOps platform continuously assesses your detection posture and eliminates coverage gaps in your existing SIEM/XDR — Splunk, Microsoft Sentinel, IBM QRadar, Google Chronicle SIEM, CrowdStrike Falcon LogScale, Sumo Logic — so you can easily implement a threat-informed defense.
What’s more, it drives cost savings and greater efficiencies by recommending new ways to tune noisy and inefficient queries, reduce logging volume, and eliminate underused tools in your stack. Learn more at cardinalops.com.