Operationalize MITRE ATT&CK in your SOC
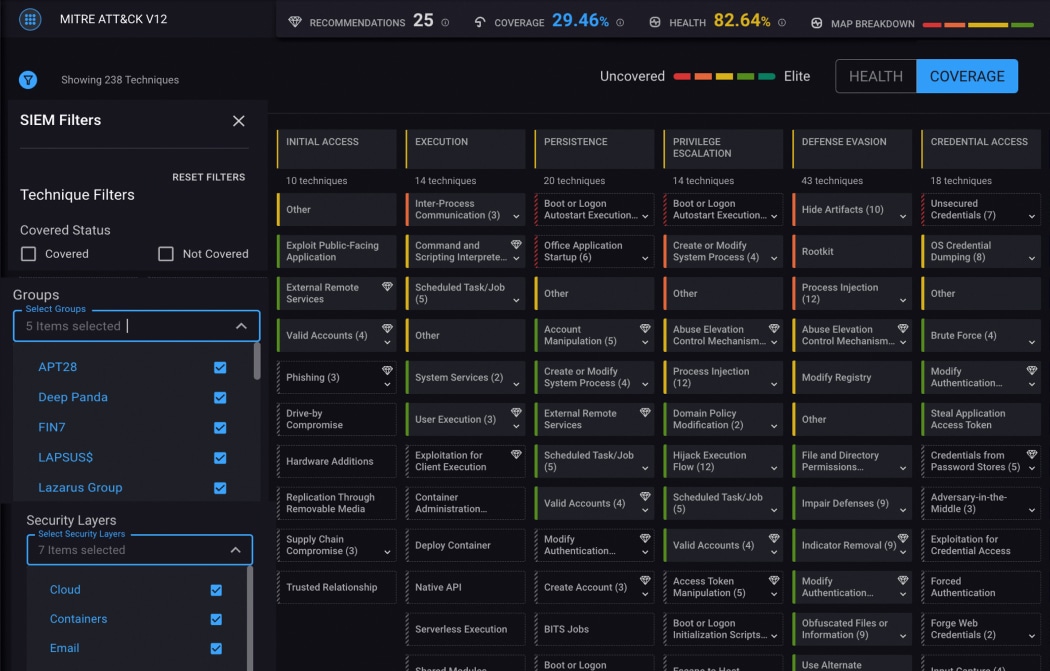
Using automation and MITRE ATT&CK, the CardinalOps platform continuously assesses your detection posture and eliminates coverage gaps in your existing SIEM/XDR (Splunk, Microsoft Sentinel, IBM QRadar, Google Chronicle SIEM, etc.) – so you can easily implement a threat-informed defense.
What’s more, it drives cost savings and efficiencies by recommending new ways to tune noisy and inefficient queries, reduce logging volume, and eliminate underused tools in your stack.

Our SaaS platform continuously audits your SIEM/XDR to maximize your detection posture and help answer key questions such as:
Do we have the right detections and
log sources, based on ATT&CK and
our organizational priorities?
What are
we not
detecting?
Are our detections and
log sources working as
they should?
How do we leverage automation
to quickly identify and fix
critical coverage gaps?
Can we reduce costs and complexity
by eliminating unused or redundant
tools from our stack?